Some mysteries don’t fade with time—they ferment.
WEDNESDAY DEEP DIVE
In May 2025, we published “How AI Solved the Zodiac Killer’s Cipher After 51 Years”—a story that captured something remarkable about the intersection of human persistence and machine intelligence. The response was overwhelming. Readers wanted more: How exactly did they crack it? What does this mean for cybersecurity? Where does AI end and human judgment begin?
This Wednesday Deep Dive expands that story into the comprehensive investigation you asked for. We dig deeper into the mathematical impossibility that stumped the FBI for five decades, the ethical tightrope of AI in criminal justice, and the cybersecurity wake-up call that governments worldwide are scrambling to address. If the original article was the headline, this is the full investigative report.
Welcome to the complete story of how three amateurs accomplished what entire government agencies couldn’t—and what their breakthrough reveals about the future we’re building together.
To keep up to date on this story and more like it, join our Mystery Lover’s Newsletter! Get behind the scenes information, detailed posts beyond what is available here, and so much more!
Sign Up Today!
For more than half a century, the Zodiac Killer’s Z340 cipher wasn’t just unsolved; it was smug. A 340-character middle finger mailed to the San Francisco Chronicle in 1969, daring the world to keep up. The FBI tried. The NSA tried. Thousands of amateur codebreakers tried. For 51 years, every attempt failed.
Until one didn’t.
On November 8, 1969, a letter arrived at the San Francisco Chronicle. Inside was a carefully arranged grid of 340 strange symbols arranged in 17 columns and 20 rows. No explanation. No key. Just menace. Accompanying the cipher was a fragment of victim Paul Stine’s bloodstained shirt—proof of authorship. The sender called himself Zodiac.
His previous cipher, the Z408, had been cracked in just eight days by Donald and Bettye Harden, a schoolteacher couple who used classical frequency analysis. That humiliation clearly stung. Because the Z340 was different—layered, irregular, and designed specifically to resist the techniques that had defeated the Z408. For decades, it mocked the FBI’s Cryptanalysis and Racketeering Records Unit, the NSA’s legendary codebreakers, professional cryptographers at universities worldwide, and thousands of obsessed amateurs working independently. It became cryptography’s Mount Everest—with worse vibes.
This is the story of how three amateur cryptographers from three different continents—armed with mathematical intuition, homemade software, and pure stubbornness—finally made the cipher speak. But more importantly, it’s about what that breakthrough reveals about artificial intelligence, the future of cybersecurity, and the optimal partnership between human judgment and machine power.
The Theater of Terror and the Architecture of Silence
Between December 1968 and October 1969, at least five people were murdered in Northern California in attacks attributed to the Zodiac Killer. The confirmed victims included teenagers David Faraday and Betty Lou Jensen at Lake Herman Road, Darlene Ferrin and survivor Michael Mageau at Blue Rock Springs Park, college students Cecelia Shepard (who died) and Bryan Hartnell (who survived) at Lake Berryessa, and taxi driver Paul Stine in San Francisco’s Presidio Heights. But what distinguished the Zodiac from other serial offenders wasn’t just violence. It was communication.
Zodiac cultivated attention through letters, phone calls, and puzzles. He demanded front-page publication. He threatened mass murder if ignored. He weaponized media coverage and exploited public fear. The ciphers weren’t incidental to this strategy—they were central to it. Cryptography offered Zodiac a way to perform intellectual dominance. By creating puzzles that law enforcement couldn’t solve, he could maintain relevance long after the murders stopped. The Z340 cipher, in particular, functioned as a monument to that ambition.
FBI profiler James R. Fitzgerald later analyzed the psychological profile, describing someone with narcissistic personality disorder with delusions of grandeur. “This is someone who needed constant validation of his superiority,” Fitzgerald explained. “The ciphers weren’t just about hiding information—they were about proving he was smarter than everyone pursuing him.” This psychological insight is crucial to understanding why the Z340 was so difficult to solve. It wasn’t designed with mathematical elegance; it was designed with human error, inconsistency, and the specific intent to frustrate standard cryptanalytic approaches.
The Z340 wasn’t broken for 51 years because it violated expectations. Classical cryptanalysis assumes rules. Zodiac broke them. The cipher layered multiple complexities that, when combined, created exponential difficulty. First, it used homophonic substitution, where multiple symbols could represent a single letter, flattening the statistical prominence of common letters like E, T, and A. Frequency analysis—the cornerstone of classical codebreaking—became useless. Second, after substitution, the letters were systematically rearranged through transposition. Even if you correctly guessed what the symbols meant, you still wouldn’t know where they belonged. Third, the text wasn’t written left-to-right, top-to-bottom. It followed a complex “decimation” pattern, moving one row down and two columns across in a toroidal grid that wrapped around edges like Pac-Man.
Perhaps most devastatingly, the Zodiac made at least one major encipherment error, shifting his transposition pattern midway through the cipher. This inconsistency was the ultimate firewall. Automated solvers failed because they assumed the killer followed his own rules perfectly. Most cryptanalytic approaches presume internal consistency—that the person creating a cipher system applies it uniformly throughout. The Zodiac’s mistake broke this assumption, creating what cryptographer David Oranchak later called a “poisoned dataset” for classical analysis.
As cryptography historian Craig Bauer observed, this combination dismantles traditional frequency analysis entirely. “When transposition is combined with substitution, even relatively simple schemes can become extraordinarily difficult to break,” he noted. The theoretical search space was astronomically large: approximately 26 to the 63rd power possible symbol mappings multiplied by 340 factorial possible character arrangements. Testing every possibility at a billion keys per second would take longer than the age of the universe—millions of times over.
The Fellowship of the Obsessed
The people who finally cracked the Z340 weren’t government agents or career cryptanalysts. They were ordinary people who became extraordinary through sheer persistence. David Oranchak, a Virginia-based web designer, had been analyzing Zodiac ciphers since 2006. He possessed no formal cryptography training, but he had fourteen years of relentless focus. Sam Blake, an applied mathematician from the University of Melbourne, Australia, joined the effort after watching one of Oranchak’s YouTube videos during COVID-19 lockdowns. And Jarl Van Eycke, a Belgian warehouse worker and self-taught programmer, had spent years developing a sophisticated cipher-solving program called AZdecrypt.
This wasn’t just a hobby; it was an obsession. As Oranchak explained, “I think I kind of caught a bug where I became hyper-focused on solving these mysteries. It’s like having some kind of obsessive-compulsive disorder where you just can’t let it go. But that persistence—that refusal to accept defeat—is exactly what was needed.” For fourteen years, Oranchak circled the cipher, building a digital repository at zodiackillerciphers.com that served as a lighthouse for other researchers. His work attracted a global community of enthusiasts who shared findings, challenged assumptions, and proposed new models.
What distinguished their approach was the combination of complementary skills that no single person possessed. Oranchak brought domain expertise, having spent years documenting Zodiac history, previous solution attempts, and cipher patterns. Blake contributed mathematical rigor, using statistical modeling and transposition theory to generate systematic hypotheses. Van Eycke provided computational power through his optimized algorithms and software development. Together, they formed a complete cryptanalytic capability. No single member could have succeeded alone, but their distributed collaboration across three continents and three time zones created something powerful.
The methodology they developed was what Oranchak described as “buckshot”—a massive-scale testing method guided by mathematical intuition. Let’s be precise about what “AI” meant in this context. This wasn’t modern deep learning with neural networks hallucinating answers. The breakthrough came from a specialized “hill climbing” algorithm—an optimization technique that starts with a random solution, makes small changes and tests if they improve the result, keeps improvements while discarding failures, repeats millions of times, and restarts from scratch when stuck at local maximums.

Van Eycke’s AZdecrypt software used something called n-gram statistics, which are frequency counts of letter sequences in English, like the bigrams TH or HE, trigrams like THE or AND, and quadgrams like TION or THAT. By scoring potential plaintexts against these patterns learned from millions of words of English text, it could recognize when random symbols started looking like actual English words. The critical innovation was automatic whitespace insertion. The algorithm didn’t just find letter patterns—it found plausible word divisions, detecting phrases like “TRYING TO CATCH ME” in strings that would look like gibberish to humans.
But AZdecrypt was blind to transposition. It could solve homophonic substitution brilliantly, but it couldn’t unscramble rearranged text. This is where Blake’s contribution proved crucial. Using the Mathematica statistical computing package from Wolfram Research, Blake generated approximately 650,000 systematic transposition variations based on mathematical constraints. He tested different “decimation” patterns—skip sequences across the grid that might reveal the original order of letters. Each variation was fed into AZdecrypt for evaluation. Most produced nonsense. A few produced intriguing partial words. One produced clear English phrases.
The Breakthrough and What It Revealed
On December 3, 2020, David Oranchak noticed something different in the output. After thousands of failed attempts spanning weeks of computational work, partial phrases began appearing in the results. He saw “HOPE YOU ARE” and “GAS CHAMBER” and “SLAVES” and “PARADICE.” Then came the phrase that changed everything: “THAT WASNT ME ON THE TV SHOW.”

This was the smoking gun. In October 1969, weeks before the Z340 cipher arrived at the newspaper, a man falsely claiming to be the Zodiac had called into the Jim Dunbar talk show on KGO-TV in San Francisco. The caller, later identified as an impostor, expressed frantic fear of the gas chamber. The real Zodiac, apparently enraged by someone stealing his thunder, used the Z340 cipher to mock this impersonator and reclaim his mythology. This historical timestamp validated the solution more powerfully than any statistical test could. Only someone with deep knowledge of the October 1969 hoax—an incident not widely known in popular culture—could reference it.
The complete decrypted message revealed the killer’s grandiosity and afterlife delusions: “I HOPE YOU ARE HAVING LOTS OF FUN IN TRYING TO CATCH ME THAT WASNT ME ON THE TV SHOW WHICH BRINGS UP A POINT ABOUT ME I AM NOT AFRAID OF THE GAS CHAMBER BECAUSE IT WILL SEND ME TO PARADICE ALL THE SOONER BECAUSE I NOW HAVE ENOUGH SLAVES TO WORK FOR ME WHERE EVERYONE ELSE HAS NOTHING WHEN THEY REACH PARADICE SO THEY ARE AFRAID OF DEATH I AM NOT AFRAID BECAUSE I KNOW THAT MY NEW LIFE IS LIFE WILL BE AN EASY ONE IN PARADICE DEATH.”
The message contained multiple validation markers that confirmed authenticity. The direct TV show reference provided historical verification. The signature misspelling “PARADICE” matched the Z408 cipher. The afterlife mythology about collecting “slaves” aligned with his known beliefs. The taunting tone mocking investigators was consistent with all Zodiac communications. The linguistic patterns matched his writing style and vocabulary. Two days later, on December 5, 2020, the Federal Bureau of Investigation’s Cryptanalysis and Racketeering Records Unit confirmed the solution’s authenticity after independent verification. The FBI had received the team’s solution before it was made public—demonstrating ethical responsibility in how the breakthrough was handled.
But here’s what the decoded text didn’t reveal: any actionable clues. There was no confession, no identity, no justice, no geographic references, no closure for victims’ families. And yet this wasn’t failure. Because the achievement wasn’t the content of the message—which was largely predictable, another Zodiac taunt. The achievement was the demonstration that some problems can only be solved when humans and machines share the load in precisely calibrated ways.
The Real Story: What AI Actually Did (and Didn’t Do)
Here’s the uncomfortable truth that technophiles and AI evangelists don’t want to hear: artificial intelligence didn’t understand the Zodiac Killer. It recognized statistical regularities in letter combinations. That’s all. The humans provided everything else that mattered: historical verification of the TV show incident, linguistic analysis of spelling patterns and grammar, ethical judgment about when and how to release the solution, interpretation of the psychological profile and investigative value, and context about why this matters for justice and closure.
Demis Hassabis, co-founder of Google DeepMind and winner of the 2024 Nobel Prize in Chemistry, makes a crucial distinction that applies perfectly to this case. AI excels at what he calls “puzzles” but struggles with “mysteries.” Puzzles have defined rules, clear solutions, and verifiable correctness—things like chess, Go, protein folding, or mathematical optimization. Mysteries require interpretation, judgment, and human context—things like determining motive, assessing credibility, or understanding historical significance. As Hassabis explained in his Nobel Prize interview, “AI is fundamentally a pattern-finding system. It can recognize regularities in data at scales humans can’t match. But it doesn’t ‘understand’ what those patterns mean. It’s the difference between recognizing that certain letter combinations are common in English versus understanding what those combinations communicate about human psychology, history, or truth.”
The Z340 solution was a puzzle with clear verification criteria. But interpreting its significance was a mystery that required human judgment. AZdecrypt had no concept of murdered victims, no understanding of grieving families, no awareness of the ethical weight of potentially identifying a killer. These human dimensions required human wisdom.
Philosopher Shannon Vallor argues that AI systems are “mirrors, not minds”—they reflect patterns in data without moral comprehension or genuine understanding. This metaphor is particularly apt for the Z340 case. AZdecrypt mirrored English language statistics learned from millions of words of training text. But it had no concept of a serial killer taunting investigators, families seeking justice for murdered loved ones, the passage of fifty-one years of unanswered questions, or the ethical responsibility of handling such information appropriately. As Vallor writes, “We cannot simply beg for more virtue. We need to redesign our technological systems to cultivate wisdom, justice, and compassion—not just efficiency and profit. AI can find patterns, but only humans can determine which patterns matter and why.”
The Z340 case demonstrates the optimal division of labor between humans and AI with crystal clarity. Humans excel at problem framing, asking questions like “What kind of cipher might this be?” They excel at hypothesis generation, proposing ideas like “Could there be a transposition layer?” They provide domain expertise, recognizing historical references like “Does this mention actual events?” They interpret results, distinguishing “Is this authentic or coincidental?” And they provide ethical oversight, deciding “How should we handle this information responsibly?” Meanwhile, AI excels at exhaustive search, testing 650,000 transposition variants that would take humans lifetimes. It excels at pattern recognition, identifying English-like letter sequences in vast solution spaces. It provides statistical scoring, quantifying how “English” a particular text appears. It offers tireless iteration, exploring millions of key combinations without fatigue. And it provides speed, accomplishing in hours what would take humans decades or centuries.
Neither is sufficient alone. The breakthrough required both working in precisely coordinated partnership. As computer pioneer Douglas Engelbart envisioned in his 1962 landmark paper “Augmenting Human Intellect,” computers should amplify and extend human capabilities rather than replace human judgment. The Z340 solution demonstrated this vision in action. The result wasn’t AI replacing human cryptographers—it was humans and AI achieving together what neither could accomplish alone.
The Cybersecurity Wake-Up Call
The Z340 case has profound implications that extend far beyond true crime and historical puzzles. The cipher was secure in 1969 but vulnerable in 2020. That fifty-one-year “shelf life” is a warning siren for modern cybersecurity. Major government agencies and cybersecurity organizations worldwide now warn about what’s called the “Harvest Now, Decrypt Later” threat—a strategy where adversaries collect encrypted data today and store it until quantum computers can break the encryption.
As the National Institute of Standards and Technology explains in its 2024 guidance on transitioning to post-quantum cryptography, “Encrypted data remains at risk because of the ‘harvest now, decrypt later’ threat in which adversaries collect encrypted data now with the goal of decrypting it once quantum technology matures. Since sensitive data often retains its value for many years, starting the transition to post-quantum cryptography now is critical to preventing these future breaches.”
The strategy is chillingly patient. Today’s adversaries steal encrypted data including sensitive emails, classified military communications, financial records, intellectual property, and personal information. They store this encrypted data for years or decades, maintaining massive archives of material they currently cannot read. They wait patiently for computational advances, particularly in AI and quantum computing, to catch up. Then they decrypt the stored secrets when they’re still valuable, potentially decades after the original theft. The U.S. Department of Homeland Security, the UK’s National Cyber Security Centre, the European Union Agency for Cybersecurity, and the Australian Cyber Security Centre all base their official post-quantum guidance on the premise that adversaries are currently executing this strategy.
The lesson for organizations is stark: assume any encryption method has an expiration date. What protects your data today may be trivially breakable in twenty years. This reality drove NIST to release its first set of post-quantum cryptography standards in August 2024. The three new Federal Information Processing Standards (FIPS 203, 204, and 205) specify quantum-resistant algorithms for key establishment and digital signatures. IBM Research notes that “data not secured today using post-quantum cryptography is vulnerable to ‘harvest now, decrypt later’ attacks, whereby bad actors steal data and store it until a cryptographically relevant quantum computer becomes available to decrypt it.”
Organizations must implement what NIST defines as “crypto-agility”—the organizational capability to rapidly upgrade cryptographic algorithms without interrupting system operations. This requires inventorying all cryptographic assets to know what you’re protecting and how, implementing algorithm flexibility so systems can switch encryption methods quickly when needed, continuously monitoring the threat landscape for advances in AI and quantum computing, testing post-quantum algorithms now rather than waiting until the threat is imminent, and planning for eventual compromise by operating under the assumption that anything encrypted today could be decrypted within ten to fifty years.
The White House National Security Memorandum 10, issued in 2022, set a target completion date of 2035 for U.S. federal systems to transition to post-quantum cryptography. The urgency reflects a mathematical reality: organizations must begin transitioning before the combination of data shelf-life, transition complexity, and quantum computing timelines converges. If quantum computers capable of breaking current encryption are a decade away, and your sensitive data must remain confidential for twenty years, and system migration takes five years—then the time to start is now.
This power is double-edged. The same computational techniques that solved the Z340 could be weaponized against modern cryptographic systems. The democratization of powerful AI tools means both defenders and attackers have access to capabilities that were science fiction a decade ago. As cryptographic systems race to outpace quantum threats, the Z340 case offers a sobering reminder: secrets thought secure for half a century can become vulnerable when computational power catches up.
When AI Hits Its Limits
Two Zodiac ciphers remain unsolved: the Z13 containing just thirteen characters and the Z32 containing thirty-two characters. They may never yield unique solutions—not because we lack better AI or more computational power, but because of fundamental mathematical impossibility.
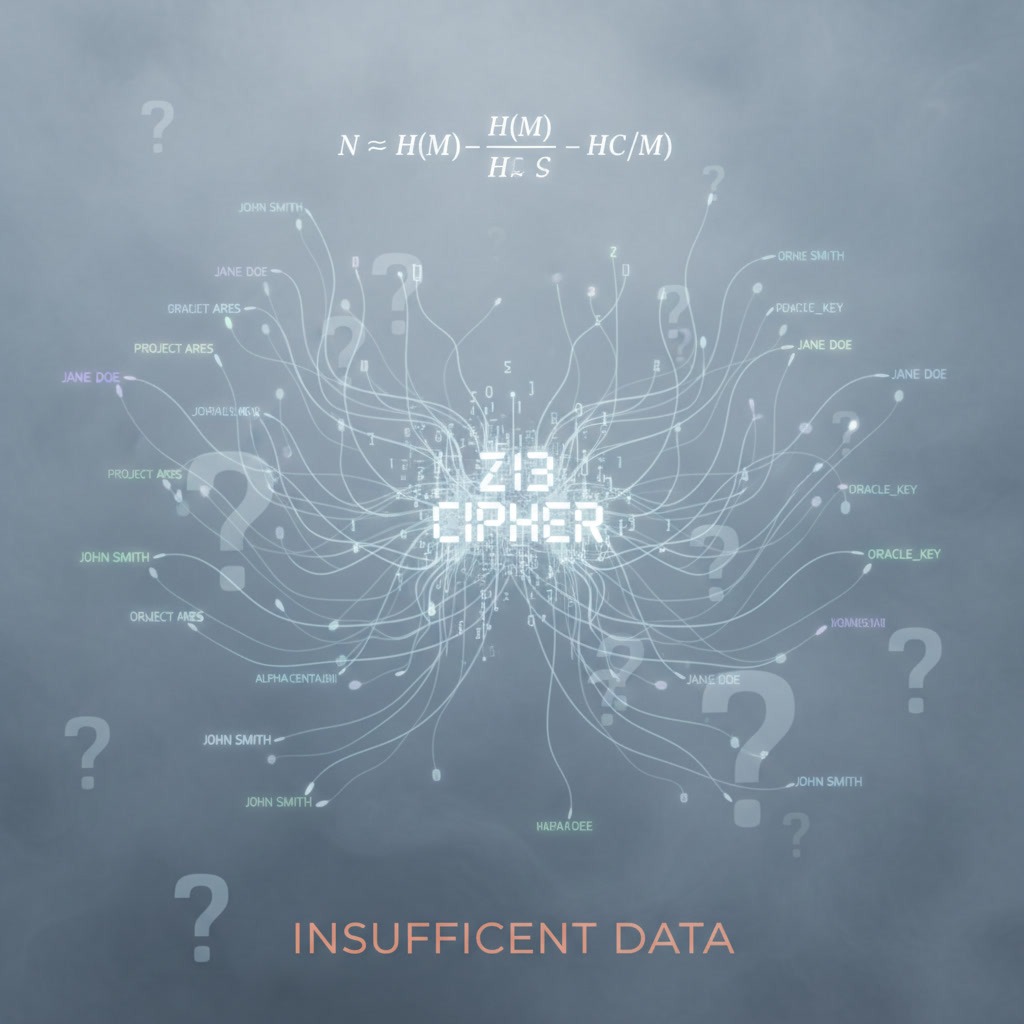
Claude Shannon, the father of information theory and modern cryptography, introduced the concept of “unicity distance” in his groundbreaking 1948 paper “A Mathematical Theory of Communication.” Unicity distance represents the minimum ciphertext length needed to guarantee a unique solution. For English substitution ciphers, that threshold is approximately twenty-seven characters. The Z13, at only thirteen characters, is well below this threshold. This means that from a pure information theory perspective, thousands of different names and phrases could theoretically fit the cipher’s pattern with equal statistical plausibility. Without additional context or independent verification, there’s simply no mathematical way to prove which solution is correct.
Over the years, various researchers have proposed Z13 solutions including “Alfred E Neuman” (the MAD Magazine mascot), “Robert Emmet” (various suspect names), “Leigh Allen” (referencing prime suspect Arthur Leigh Allen), and dozens of other possibilities. All of them are statistically valid. The problem isn’t that the Z13 has too few solutions—it’s that it has too many. As David Oranchak explains, “Short ciphers are cryptographic nightmares. The longer the text is, the more constraints you have, the more patterns emerge, and the fewer valid solutions exist. But with only thirteen characters, thousands of different plaintexts could produce the exact same ciphertext. There’s simply not enough information to uniquely determine the answer.”
The Z32 cipher, sent in June 1970 and called the “Map Cipher” because it accompanied a map claiming to show a bomb location, presents similar challenges. At thirty-two characters, it’s only slightly above Shannon’s unicity distance, meaning multiple plausible solutions could exist. Additionally, the cipher may use hybrid encryption that depends on coordinates from the accompanying map, creating a two-stage encryption where solving the symbols requires geographic reference points. Many researchers suspect this was a bluff where the Zodiac created meaningless symbols to maintain his mystique after the murders had stopped. No bomb was ever found.
Demis Hassabis makes an observation that applies directly to these unsolved ciphers and reveals AI’s fundamental limits: “AI systems are information-processing machines. If the information isn’t there—if the data is insufficient or the problem is ill-defined—even the most powerful AI is just a very fast guesser. The Z13 and Z32 ciphers might never be solvable because there’s simply not enough data to uniquely determine a solution. No amount of AI power can manufacture information that doesn’t exist in the data itself.”
This represents a boundary that no amount of technological advancement can cross. Some problems genuinely don’t have unique solutions. Some mysteries remain mysteries not because we lack the tools to solve them, but because they’re fundamentally underdetermined by the available evidence. Accepting these limits with intellectual humility is as important as pushing boundaries with technological ambition.
The Ethical Tightrope
The Z340 breakthrough has reinvigorated interest in AI-assisted cold case investigations, and law enforcement agencies worldwide are exploring how similar computational techniques might help with forensic linguistic analysis, pattern recognition in evidence databases, genomic analysis using family DNA trees, behavioral profiling across geographic and temporal data, and digital forensics for encrypted communications. But this capability raises profound ethical questions that the solving team navigated with care.
Europol, the European Union’s law enforcement agency, published comprehensive guidelines titled “Artificial Intelligence and Policing” that establish six core principles for ethical AI deployment. First, AI systems must respect fundamental rights including privacy, fair trial guarantees, and freedom from discrimination—the technology’s capabilities don’t override constitutional protections. Second, they must prevent discrimination through regular audits to detect biased patterns in training data or algorithmic outputs. Third, they require transparency, meaning AI decision-making processes must be explainable to suspects, defendants, judges, and the public; black box systems that cannot articulate their reasoning are inappropriate for criminal justice. Fourth, clear chains of human accountability must exist for all AI outputs—no algorithm should make final decisions without human oversight and review. Fifth, systems must demonstrate accuracy and reliability through rigorous testing against ground truth data and continuous monitoring for errors. And sixth, training data must be representative, unbiased, and lawfully obtained while using privacy-preserving techniques that minimize data collection and retention.
A comprehensive Florida State University Law Review article provides critical analysis of AI’s risks in law enforcement. The authors identify several specific concerns including bias amplification, where AI systems trained on historical crime data inevitably inherit biases from decades of discriminatory policing practices. If certain communities were historically over-policed, AI systems will identify those areas as “high-crime” and recommend more policing, creating self-fulfilling prophecies. There are constitutional concerns about the Fourth Amendment protection against unreasonable search and seizure and the Fourteenth Amendment’s equal protection clause, which place constraints on how AI can be used in investigations. Algorithmic predictions alone cannot justify searches without individualized suspicion. The framework emphasizes that “efficient use of AI must be balanced against fundamental rights. Algorithmic predictions can become self-fulfilling prophecies that entrench inequality.”
Consider the ethical minefield of forensic genomics, which uses family DNA databases to identify criminals. This technique involves obtaining DNA from crime scenes, searching commercial genealogy databases like 23andMe or Ancestry, identifying partial matches with relatives who voluntarily submitted DNA, building family trees to narrow suspect pools, and conducting targeted surveillance. This approach has solved several cold cases including the Golden State Killer in 2018, but it raises profound privacy concerns. People who never consented to law enforcement searches can be implicated because their relatives submitted DNA for genealogy research. Every person’s DNA becomes a potential surveillance tool not just for them, but for their entire extended family including future generations not yet born. Databases created for one purpose—genealogy research—are being repurposed for law enforcement without explicit user consent or clear legal frameworks. And genetic databases disproportionately represent certain demographics, potentially creating biased investigative focus.
The Z340 solving team demonstrated ethical best practices that should serve as a model. They submitted their solution to the FBI before publicizing it, demonstrating accountability and respect for the investigative process. They explained their methodology in peer-reviewed academic publications, providing transparency that allows verification and builds scientific knowledge. They verified results against historical evidence rather than relying solely on statistical tests, ensuring accuracy through multiple validation methods. And they respected victims’ families by maintaining appropriate tone in public communications, recognizing the human tragedy behind the mathematical puzzle. These were human ethical choices, not algorithmic outputs. No AI system would spontaneously decide to contact the FBI first or maintain respectful language about murder victims. These are fundamentally human moral judgments that cannot be delegated to algorithms.
What We’ve Learned
The Zodiac Killer wanted to be remembered as clever, superior, unknowable—a criminal mastermind who could outwit entire government agencies with pencil-and-paper cryptography. Instead, he became a case study in something far more interesting: the limits of human cruelty and the power of human persistence, the optimal partnership between human expertise and machine computation, the ethical challenges of deploying powerful technology in sensitive contexts, the democratization of problem-solving through open collaboration, and the shrinking shelf life of encrypted secrets in an age of computational abundance.
The cipher didn’t fall because AI was brilliant. It fell because people refused to quit, refused to accept that the puzzle was unsolvable, and learned how to harness computational tools without surrendering human judgment. As Alan Turing observed decades ago, “It’s the people no one imagines anything of who do the things that no one can imagine.” None of the solving team members held advanced degrees in cryptography or worked for government agencies or prestigious research institutions. They were a web designer, a mathematician who joined during lockdown boredom, and a warehouse worker who programmed in his spare time. What they had wasn’t credentials—it was complementary skills, persistence across years of failure, and the wisdom to combine human judgment with machine power in the right proportions.
The template they’ve given us for the age of AI is clear. Let AI amplify human capability, but never replace human judgment. Let machines explore vast solution spaces that would take humans lifetimes to traverse, but let humans determine which solutions actually matter and why. Let computational power accelerate our search for truth and justice and understanding, but let human conscience guide how we use the truths we find and what we do with the power we wield.
Artificial intelligence can search faster than we ever will. It can analyze more data than we can process. It can test more hypotheses than we have time to consider. But only humans know why the search matters. Only humans can weigh the moral dimension of our computational capabilities. Only humans can decide which problems deserve solving and how solutions should be deployed in service of justice rather than oppression.
The cipher that waited fifty-one years to speak has taught us that the future of problem-solving isn’t artificial intelligence alone—it’s augmented intelligence, where humans and machines each contribute what they do best in carefully calibrated partnership. And that might be the most human pattern of all: our willingness to build tools that extend our reach without surrendering our responsibility, to pursue knowledge without abandoning wisdom, and to wield power without forgetting conscience.
The Zodiac wanted to be remembered for mystery. Instead, he’ll be remembered for teaching us how to solve mysteries together—human and machine, working in partnership to bring light to darkness, one pattern at a time.
References
- Bauer, C. P. (2014). Unsolved!: The history and mystery of the world’s greatest ciphers. Princeton University Press.
- Blake, S. (2024, April 4). Sleuths who cracked Zodiac Killer’s cipher thank the crowd. The Register. https://www.theregister.com/2024/04/04/zodiac_killer_code/
- Engelbart, D. C. (1962). Augmenting human intellect: A conceptual framework. Stanford Research Institute.
- Europol. (2020). Artificial intelligence and policing: Challenges and opportunities. European Union Agency for Law Enforcement Cooperation. https://www.europol.europa.eu/publications-events/publications/artificial-intelligence-and-policing
- Federal Bureau of Investigation. (2020, December 11). Statement regarding Zodiac cipher. FBI San Francisco Division.
- Florida State University Law Review. (2022). A framework for the efficient and ethical use of artificial intelligence in the criminal justice system. Florida State University Law Review, 49(3), 1287–1342.
- Graysmith, R. (2007). Zodiac. Berkley Books.
- Hassabis, D. (2024, October 9). Nobel Prize lecture: Accelerating scientific discovery with AI. NobelPrize.org. https://www.nobelprize.org/prizes/chemistry/2024/hassabis/lecture/
- Hodges, A. (1983). Alan Turing: The enigma. Simon & Schuster.
- IBM Research. (2024, August 13). NIST’s post-quantum cryptography standards are here. IBM Research Blog. https://research.ibm.com/blog/nist-pqc-standards
- Mascelli, J., & Rodden, M. (2025). “Harvest Now Decrypt Later”: Examining post-quantum cryptography and the data privacy risks for distributed ledger networks. Finance and Economics Discussion Series 2025-093. Board of Governors of the Federal Reserve System. https://doi.org/10.17016/FEDS.2025.093
- National Institute of Standards and Technology. (2024). Transition to post-quantum cryptography standards (NIST IR 8547). U.S. Department of Commerce. https://nvlpubs.nist.gov/nistpubs/ir/2024/NIST.IR.8547.ipd.pdf
- National Institute of Standards and Technology. (2024). What is post-quantum cryptography? NIST Cybersecurity. https://www.nist.gov/cybersecurity/what-post-quantum-cryptography
- Oranchak, D., Blake, S., & Van Eycke, J. (2024). Solving the Zodiac Killer’s 340-character cipher. Cryptologia, 48(2), 129–157. https://doi.org/10.1080/01611194.2024.2312304
- Shannon, C. E. (1948). A mathematical theory of communication. Bell System Technical Journal, 27(3), 379–423.
- Vallor, S. (2016). Technology and the virtues: A philosophical guide to a future worth wanting. Oxford University Press.
- Vallor, S. (2024). The AI mirror: How to reclaim our humanity in an age of machine thinking. Oxford University Press.
- Virginia Tech Engineering Magazine. (2021, Spring). The new cryptographers. https://eng.vt.edu/magazine/stories/spring-2020/the-new-cryptographers.html
- The White House. (2022). National Security Memorandum 10: Promoting United States leadership in quantum computing while mitigating risks to vulnerable cryptographic systems. https://www.whitehouse.gov/briefing-room/statements-releases/2022/05/04/national-security-memorandum-on-promoting-united-states-leadership-in-quantum-computing-while-mitigating-risks-to-vulnerable-cryptographic-systems/





Leave a Reply